Your network will only run as well as the slowest component, so if it is under specified, poorly installed, utilises poor technology or is just not up to the job anymore, your entire operation will suffer. Our experienced team of network experts will be able to quickly diagnose where problems lie and will support you as you look to improve.
Password Attacks
Structured Attacks
Unstructured Attacks

Eavesdropping Attacks
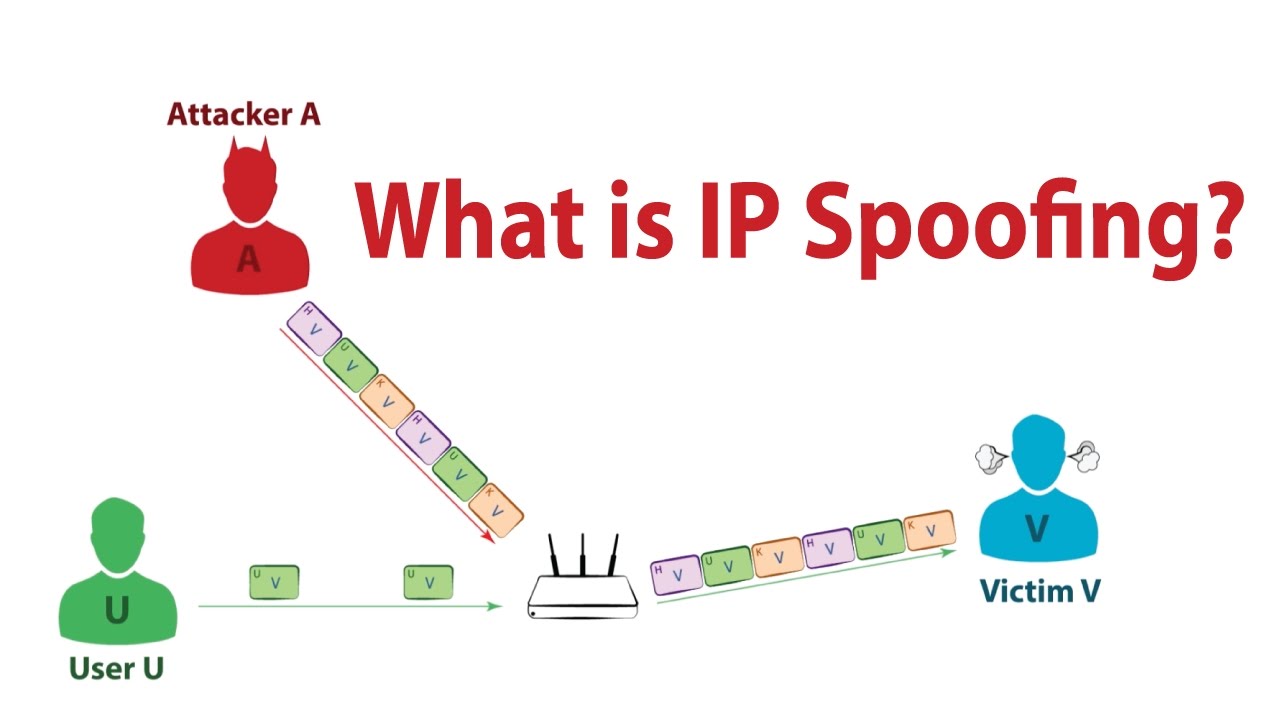
IP Address Spoofing Attacks
Social Engineering Attacks


 English
English  French
French  German
German  Italian
Italian